Assumptions
It is assumed the following products have been installed:Oracle RDBMS 11gR2 - holding metadata
Oracle Unified Directory 11.1.2.2.0 - LDAP for system and user store
Oracle Access Manager 11gR2PS2
Weblogic 10.3.6
Oracle OHS (which if I recall is installed with Weblogic)
Webgate 11g installed and configured
My environment consists of three RHEL 5.10 x64 VMs consisting of svrtoes01, svrtst02, and svrtst03 as follows:
Oracle RDBMS 11gR2 on server svrtoes01
Components installed for supporting the FMW (fusion middleware) stack are:
COMP_ID OWNER VERSION MODIFIED U
-------------------- -------------------- ----------------- ---------- -
APM SYSMAN_APM 11.1.1.3.0 2014-03-05 N
MDS SYSMAN_MDS 11.1.1.6.1 2014-03-05 N
OPSS SYSMAN_OPSS 11.1.1.6.0 2014-03-05 N
IAU DEV_IAU 11.1.1.7.0 2014-04-30 N
MDS DEV_MDS 11.1.1.7.0 2014-04-30 N
OAM DEV_OAM 11.1.2.2.0 2014-04-30 N
OID ODS 11.1.1.7.0 2014-04-30 N
OPSS DEV_OPSS 11.1.1.7.2 2014-04-30 Y
OIM DEV_OIM 11.1.2.2.0 2014-05-08 N
ORASDPM DEV_ORASDPM 11.1.1.7.0 2014-05-08 N
SOAINFRA DEV_SOAINFRA 11.1.1.7.0 2014-05-08 N
See this link on what is installed on svrtst02 and svrtst03:
http://anotherdatabaseblog.blogspot.com/2014/05/oracle-access-manager-oam-111220-and.html
There are many resources on the web that show detailed instructions on how to install various components of the Oracle FMW stack. I have found these to be very useful:
http://www.iamidm.com
http://fusionsecurity.blogspot.com
http://www.ateam-oracle.com
http://onlineappsdba.com
An 11g webgate was installed:
http://anotherdatabaseblog.blogspot.com/2014/05/create-and-deploy-11g-webgate.html
I used this link http://www.iamidm.com/2012/10/oam-11g-r2-lab4-protecting-secure-url.html to help me in setting up and testing access to a secure web page. This link shows you how to setup a webpage hosted on OHS and protected by OAM. I just extend the example to include X509 authentication.
However, in order to protect the resource and only allow access via X509 certificates, some changes are required in OAM. To be clear, this exercise shows how to do X509 authentication (AUTHN) to allow access to a resource, in this case a simple web page.
It is assumed that Weblogic and OAM have been configured for SSL and that you have access to certificates issued by a CA (http://fusionsecurity.blogspot.com/2011/02/certificate-x509-authentication-in-oam.html).
Add Root and Intermediate Certificates to .oamkeystore
The oamkeystore is Access Managers keystore and is located in $MW_HOME/user_projects/domains/WLSDomain/config/fmwconfig/.The root and intermediate (if any) certificates need to be installed for X509 authN to work.
First, get the password for the keystore as follows:
cd $MW_HOME/Oracle_IDM1/common/bin
./wlst.sh
connect()
domainRuntime()
listCred(map="OAM_STORE",key="jks")
Make a note of the password and then exit scripting tool
exit()
Install the root and intermediate certificates. In my setup, I have my certs located in the /certs directory. The root certificate is in a file called ISEDlabRoot.crt and the intermediate certificate is in a file called CADCA1.crt. I need to change to the location where my certs are installed:
cd /certs
Then run the command to import the certs into the keystore:
keytool -importcert -alias ISEDlabRoot -file ISEDlabRoot.crt \
-keystore $MW_HOME/user_projects/domains/WLSDomain/config/fmwconfig/.oamkeystore \
-storepass oa6fgome4lsnf9c6ntoio1qc5p -storetype jceks
Answer 'yes' when prompted whether to trust this certificate
Successful import will respond with: Certificate was added to keystore
Import the intermediate cert into the keystore:
keytool -importcert -alias CADCA1 -file CADCA1.crt \
-keystore /opt/oracle/middleware/user_projects/domains/WLSDomain/config/fmwconfig/.oamkeystore \
-storepass oa6fgome4lsnf9c6ntoio1qc5p -storetype jceks
Successful import will respond with: Certificate was added to keystore
Configure Web Pages
I have two web pages:secure.html
<i><html></html></i>
<i><body></body></i>
<i><a href="http://10.10.107.89:7777/logout2.html?end_url=">Logout</a></i>
<i></i>
<center>
<i> <h1>
This is Secure Page, Only logged in users can view </h1></i></center><i> </i>
<i></i></div><i></i>
<i>
</i> Name it as <b>sample.html</b>
<b>
</b>
logout2.html
<i><html></html></i>
<i><body></body></i>
<i><b><span style="color: red;"><a href="http://10.10.107.89:7777/logout2.html?end_url=">Logout</a></span></b></i>
<i></i>
<center>
<i> <h1>
This is Secure Page, Only logged in users can view </h1></i></center><i> </i>
<i></i>
<i></i>
These are installed $MW_HOME/Oracle_WT1/instances/instance1/config/OHS/ohs1/htdocs. Note that end_url= is left blank when configured for X509 authN.
Configure Oracle Access Management
Login to the Oracle Access Management consoleFrom Launch Pad -> Access Manager -> Application Domains
Click Search
Select RREG_OAM11G then click the edit icon
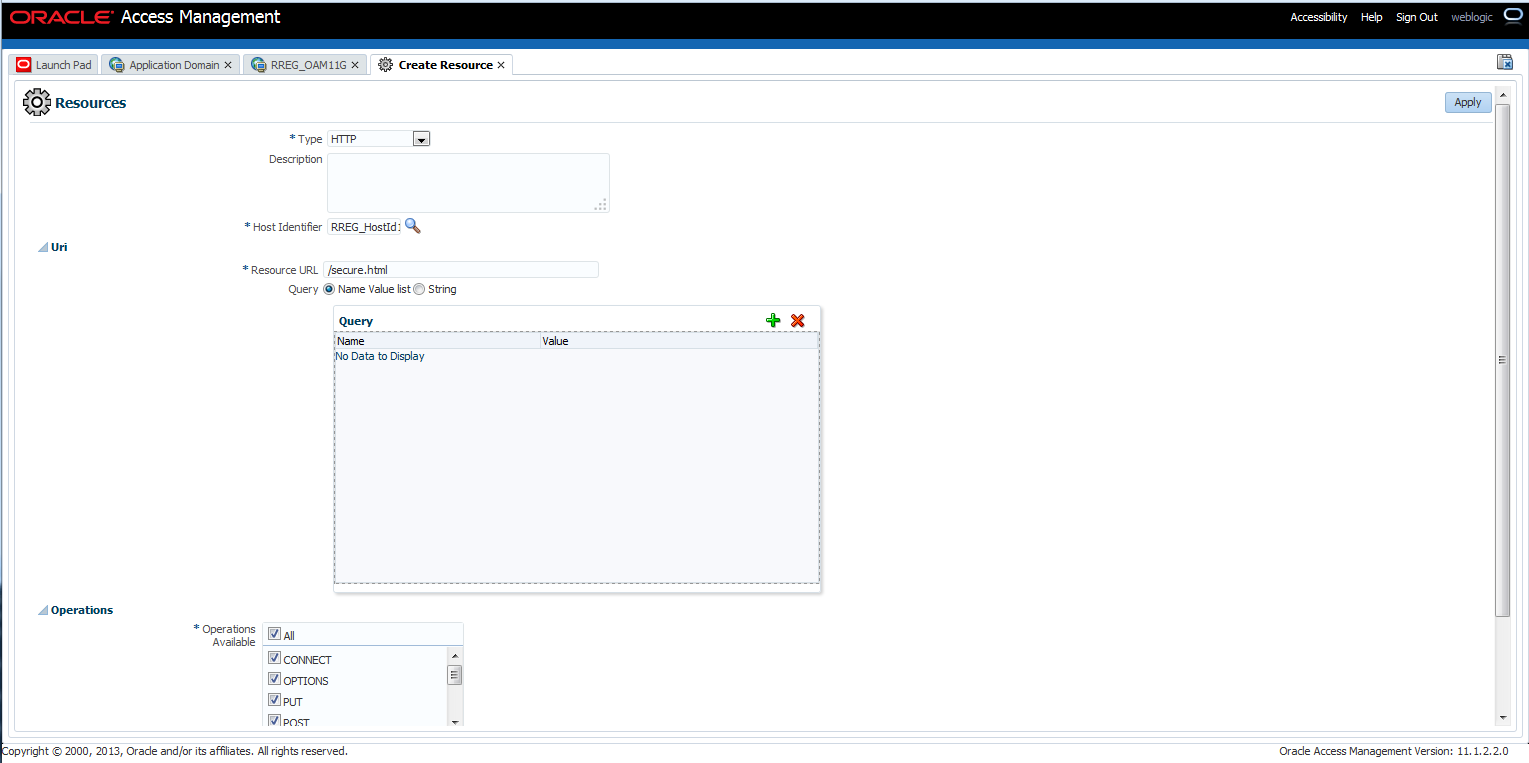
Click on Resources tab, then click Create
Select HTTP from the Type drop down
Host Identifier can be searched for using the search icon. Enter RREG_HostId11G in the Host Identifier field
Enter /secure.html in Resource URL. This is the resource that is going to be protected
Select Protected for Protection Level
Click Apply to continue
Close the RREG_OAM11G: RREG_HostID... tab
Click on the Autentication Policies tab then click on the Create Authentication Policy button
Enter a name for the policy, e.g X509_Test
Select X509Scheme for Authentication Scheme
The new policy will be displayed
Click on the Resources tab and the newly added resource that needs to be protected (secure.html) will be displayed. Note that the new resource is not attached to any policy yet
Next, attach the resource to the newly created authentication policy. Select the resource (secure.html) in the grid and click the Edit button.
From the Authentication Policy drop down, select X509_Test and click Apply
Close the RREG_OAM11G:RREG_HostId... tab
In the RREG_OAM11G tab, click the Search button which will show that secure.html is protected by the new X509_Test authentication scheme
Restart the OAM server for the changes to take effect
Now try and access the protected resource, secure.html in this case which hosted on http://10.10.107.89:7777/secure.html. The HTTP request will be intercepted by the 11g Webgate and routed to OAM which will prompt you to present a client certificate:
The protected web page will be displayed:
Click the Logout link and you will be logged out and all session cookies will be removed:
You can view the Oracle Unified Directory (OUD) access_log located $OUD_HOME/logs and see the connection to the LDAP being made the the user CN being verified:
[21/May/2014:15:50:04 -0400] SEARCH REQ conn=29429 op=15 msgID=16 base="dc=acme,dc=com" scope=sub filter="(&(objectclass=inetOrgPerson)(cn=weblogic))" attrs="uid,wirelessacctnumber,postalcode,manager,street,orclguid,obresponsetries,dateofbirth,uniquename,defaultgroup,telephonenumber,obresponsetimeout,orgunit,timezone,employeenumber,obYetToBeAnsweredChallenge,initials,activestartdate,description,maidenname,localityname,gender,objectclass,sn,oblastloginattemptdate,fax,middlename,homeaddress,country,obpasswordhistory,cn,oblastsuccessfullogin,oblastfailedlogin,preferredlanguage,pobox,mobile,hiredate,uiaccessmode,oblastresponseattemptdate,department,state,givenname,lastname,org,employeetype,title,obfirstlogin,name,obpasswordcreationdate,homephone,pager,mail,activeenddate,oblockouttime,obAnsweredChallenges,loginid,firstname,obpasswordexpmail,obpasswordchangeflag,postaladdress,obuseraccountcontrol,telephone,displayname,oblogintrycount"
[21/May/2014:15:50:04 -0400] SEARCH RES conn=29429 op=15 msgID=16 result=0 nentries=1 etime=2
[21/May/2014:15:50:04 -0400] SEARCH REQ conn=29430 op=4 msgID=5 base="cn=weblogic,cn=systemids,dc=acme,dc=com" scope=base filter="(objectclass=inetOrgPerson)" attrs="uid,wirelessacctnumber,postalcode,manager,street,orclguid,obresponsetries,dateofbirth,uniquename,defaultgroup,telephonenumber,obresponsetimeout,orgunit,timezone,employeenumber,obYetToBeAnsweredChallenge,initials,activestartdate,description,maidenname,localityname,gender,objectclass,sn,oblastloginattemptdate,fax,middlename,homeaddress,country,obpasswordhistory,cn,oblastsuccessfullogin,oblastfailedlogin,preferredlanguage,pobox,mobile,hiredate,uiaccessmode,oblastresponseattemptdate,department,state,givenname,lastname,org,employeetype,title,obfirstlogin,name,obpasswordcreationdate,homephone,pager,mail,activeenddate,oblockouttime,obAnsweredChallenges,loginid,firstname,obpasswordexpmail,obpasswordchangeflag,postaladdress,obuseraccountcontrol,telephone,displayname,oblogintrycount"
[21/May/2014:15:50:04 -0400] SEARCH RES conn=29430 op=4 msgID=5 result=0 nentries=1 etime=2
Also, in the oam_server1.out log located $MW_HOME/user_projects/domains/WLSDomain//servers/oam_server1/logs, you can view the SSL key negotiation and exchange in progress and verification of the certificates. This is only true if SSL debugging is turned on.
And in $MW_HOME/Oracle_WT1/instances/instance1/diagnostics/logs/OHS/ohs1 the access_log will show the initial connection being made as the user requests the resource.













This comment has been removed by a blog administrator.
ReplyDelete